13/05/2011
Fosswar 2011 – How we did it
Intro
As said in my previous post about Fosscomm 2011, during the conference there was a wargame consisting of 5 challenges. We played in a team consisting mainly of the following members: manji/manjiki, trelo_mpifteki, mickflemm and me. Along with us was maisk mainly acting as our manager (!!) shouting at us when we did something he did not like. He was of course a great help (sometimes :P).
Few words about the team
As most people who regularly read this blog already know, I consider myself a sysadmin even though I currently work at a company that produces Linux based xDSL routers where I do most of the things required about networking and system interaction like QoS, VoIP, IPv6, firewall, etc. My coding is confined among the realms of scripting languages. Manji is also a sysadmin who has lately started to mess with VoIP. Trelo_mpifteki is mostly a java developer and so is maisk. mickflemm is a coder and a very good one, frequently messing with Linux kernel’s wireless driver support. Obviously, we are certainly not the typical wargame players…
The challenges
Be sure to download the challenges from: http://patras.fosscomm.gr/fosswar/
As soon as the wargame was on we split the challenges among us. Since mickflemm was the only coder he started to mess with challenge number 5 (reverse engineering). Me and trelo_mpifteki started to look at challenge number 1 (networking) while manji started poking at challenge number 3 (networking).
Challenge 1:
Type: Networking
Players: kargig, trelo_mpifteki
The first challenge said just this:
Connect to the elite port and find the secret message.
Everyone knows that elite = 31337
So we just did a nc X.Y.Z.W 31337 (where X.Y.Z.W is the IP address of the server) and the following message appeared:
IP protocol = 1
Timestamp
id = 1337
seq = 0xCAFE
orig = 0xDEAD
As it is easily understood one must create a packet, the problem is what kind of packet. And then was when I did a huge mistake stalling my team for more than 10 mins by insisting that Protocol 1 is IP. So we started trying to create an IP packet using scapy. Obviously we hit lots of problems because IP’s header clearly misses most of the above options, especially timestamp. Our next idea was to create a TCP packet in order to embed some of the options. This also lead to a dead end. The I looked again at my /etc/protocols file and I saw that Protocol 1 is ICMP. Timestamp is type 13, code 0 and the rest are just options. So our solution was this:
>>> packet_2= IP(dst='X.Y.Z.W')/ICMP(type=13, id=1337, seq=0xcafe, ts_ori=0xdead) >>> send(packet_2)
Using Wireshark we captured the response packet which looked like this (this setup is on my box atm):
One can see the message: feedadeadface in it.
Hint:
If you need to compile listenicmp.c yourself you have to do something like this:
# aptitude install libpcap-dev # gcc -o listenicmp listenicmp.c -lpcap
Challenge 2:
Type: Steganography
Players: kargig,trelo_mpifteki,maisk
For this challenge the organizers gave us a hint what we needed to find was close to the end of the image.jpg and after “BAADF00D”.
# hd image.jpg | tail -n 4 000152a0 d4 4d 77 22 b9 9a 68 ba ad f0 0d 78 9c 0b c9 c8 |.Mw"..h....x....| 000152b0 2c 56 00 a2 44 85 e2 d4 e4 a2 d4 12 85 dc d4 e2 |,V..D...........| 000152c0 e2 c4 f4 54 3d 00 72 da 08 ef |...T=.r...| 000152ca
so we found “ba ad f0 0d” and the next characters were “78 9c”. We googled those and came up with the result that it was the magic of zlib compression. So what we had to do was get the rest of the file after “ba ad f0 0d” and then uncompress that. To get the rest of the file we found the size of the file and subtracted the bytes (31) that were of interest to us:
# du -b image.jpg 86730 image.jpg # split -b 86699 image.jpg koko # mv kokoab final
Then we run python to decompress “final” file.
>>> import zlib >>> ourfile=file('final') >>> ourfile <open file 'final', mode 'r' at 0xb7473020> >>> chunk=ourfile.read() >>> chunk 'x\x9c\x0b\xc9\xc8,V\x00\xa2D\x85\xe2\xd4\xe4\xa2\xd4\x12\x85\xdc\xd4\xe2\xe2\xc4\xf4T=\x00r\xda\x08\xef' >>> zlib.decompress(chunk) 'This is a secret message.'
Challenge 3:
Type: Networking
Players: manji,maisk,kargig
While me and trelo_mpifteki were trying to solve challenges 1 and 2, manji was looking into challenge 3 pcap file for weird things. Once again we were given a hint that we needed to look at strange headers. Finding strange headers in a 800+ kb pcap file is not an easy task though. At a point manji was looking for very big sequence numbers…and then we got another hint, that we shouldn’t look at those big numbers at all. When me and trelo_mpifteki finished the other two challenges we started looking at Wireshark.
We applied the following filter:
(ip.host == 64.22.109.100) && ((tcp.seq == 0) || (tcp.seq ==1))
And the we had the following results in front of us:
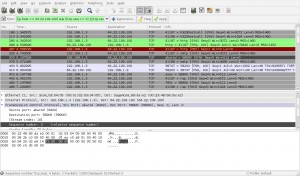
Since we knew that the message was sent to “64.22.109.100” we needed to look at packets originating from “192.168.1.3”. The first thing I noticed were packets with strange TTLs, they were going up and down..so I made a guess that the secret message could be hidden there. Transforming those TTL values to ASCII was a dead end. Then we started to look closer at every packet that 192.168.1.3 sent to 64.22.109.100 and we grouped them by destination port. There was clearly something going on with destination port 58900. A careful eye will also notice that packets towards port 58900 don’t have an MSS set while others mostly do. So, we expanded our filter with packets that also had destination port 58900:
((ip.host == 64.22.109.100) && ((tcp.seq == 0) || (tcp.seq ==1))) && (tcp.dstport == 58900)
and came up with this:
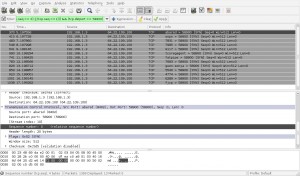
If you look closely at the selected packet from Wireshark, you’ll see that the sequence number while set to 0 (zero) contains the letter ‘r’ inside it. The next packet contained the letter ‘o’ and the next one the letter ‘t’. Writing all these letters down we had this sequence:
r
o
tq
r
n
q
o
r
r
s
That was a rot13 encrypted message! with google’s help we found a rot13 decryptor. The decrypted message was:
D E A D B E E F
That’s it! we had 3 out of 5 while no other team had more than 2. So we had wooooon! Congrats to everyone on our team!
 Filed by kargig at 11:41 under Encryption,General,Internet,Linux,Networking,Privacy
Filed by kargig at 11:41 under Encryption,General,Internet,Linux,Networking,Privacy
Tags: fosscomm, Fosscomm 2011, fosswar, hd, hexdump, icmp, maisk, manji, mickflemm, Networking, rot13, scapy, split, steganography, trelo_mpifteki, wargame, wireshark
 7 Comments | 10,189 views
7 Comments | 10,189 views

Congrats! Nice reading too.
Challenge 5
hyperion:[nous]:/tmp/fosswar/0x5% ./6275796D656162656572-v2 buymeabeef
you didn’t really think it was going to be that easy, did you?
feel free to buy me a beer though…
Shite, tbh 🙂
[…] Fosswar 2011 – How we did it […]
1st, congrats!
2nd, rot13 is also supported by your favorite editor (yes… vim). Just mark some text and press g? 😉
Great reading & congratulations!
how to hide compressed zlib to image like Challenge 2 ??